State of Retail: Why Jewelers Need to Invest in Cybersecurity Now
As cybercrime incidents threaten the industry, jewelers need to know what they’re up against and the best ways to protect their businesses.

From safes to showcases, security is one of a jeweler’s most critical investments, but many in the industry lack proper protection against a veritable army of invisible intruders.
Cybercriminals are a growing threat to businesses and governments worldwide, emptying bank accounts and holding customer information for ransom.
Protecting your business from cyberattacks is a complex task, accomplished using a mix of software, employee education, cyber liability insurance, and other tools.
National Jeweler spoke with security and insurance experts about the best ways for jewelers and their employees to stay safe online and guard their businesses.
The jewelry industry needs more cybersecurity education.
Independent, family-owned businesses can be a wealth of information, carrying on generational know-how and exhibiting top-tier customer service skills that rival, or even best, their big-name competitors.
What many lack in comparison, however, is cybersecurity expertise.
“Cybercrime experts say it is more accurate to say ‘when’ versus ‘if’ when talking about a cyberattack.” — Grant Hansen, Jewelers Mutual
A 2022 Nationwide Insurance survey found that just over half (56 percent) of small business owners offer cybersecurity training once a year, compared with 94 percent of middle-market companies.
Less than 30 percent of those surveyed said they have cyber liability insurance, compared with 83 percent of middle-market firms.
Independent jewelers far too often slip into the cybersecurity learning gap.
“I would say generally they are not well informed,” says Ryan Ruddock, senior crime analyst at the Jewelers’ Security Alliance.
“We haven’t had a very large sample size, but we have had enough that I would say jewelers still need to have ongoing education and increased awareness to prevent future [cybercrime] incidents from occurring.”
Jewelers Mutual’s Chief Information Security Officer Grant Hansen says cybercrime is beginning to show up on jewelers’ radars as the frequency of incidents increases, but the subject can “take a back seat to the more high-profile concerns affecting jewelers, such as burglary and robbery.”
However, a cybercrime attack can be just as costly, both monetarily and to a jeweler’s reputation.
The Nationwide survey found that, on average, cyber liability claims range from $15,000 to $25,000. The average recovery time for a business is 279 days— three-quarters of a year.
Notably, 76 percent of consumers surveyed said they would stop doing business with a company responsible for a data breach that impacted them.
“Every business, large or small, needs to stay vigilant to cybercrimes and keep cybersecurity top of mind with staff. Cybercrime experts say it is more accurate to say ‘when’ versus ‘if’ when talking about a cyberattack. Jewelers need to prepare accordingly,” says Hansen.
Social engineering and phishing schemes are growing threats.
Phishing, the practice of sending emails pretending to be a reputable company under the guise of stealing personal information like passwords and credit card numbers, may sound familiar, but there is another, more sinister layer to the scheme jewelers need to know about.
Social engineering, a form of impersonation, adds a level of complexity to phishing scams.
“Social engineering has been referred to as ‘the art of human hacking’ and it entails individuals researching members of the company, their positions, their job functions, and then impersonating them through emails,” says Ruddock.
It’s a more targeted form of phishing wherein the criminal is doing in-depth research into a jeweler and their business in order to attempt to defraud them.
Pretending to be a known contact or supplier, the phishing email will ask the recipient to make a payment or send out jewelry.
“The specific research the cybercriminals are doing, which is also known as pretexting, has been something they’ve had a considerable amount of success with in specific cases,” says Ruddock.
While some phishing schemes target an individual, most don’t. Often, a mass email is sent with the idea that some percentage of recipients will fall for it.
Phishing schemes, sophisticated or not, are one of the most common cybercrimes affecting jewelers, he says, and there are key things to be wary of when an email is received.
Red flags include misspellings and poor grammar, as well as emails that create a sense of urgency, pushing the recipient to do something quickly and without thinking.
Be wary of email spoofing, which is when an email is sent from an address that’s almost, but not quite, identical to a genuine email address for a contact. Two lowercase letter “n”s side by side are commonly used to mimic “m,” notes Ruddock as an example.
A good rule of thumb is to delete any email that doesn’t look right and verify the request with the vendor or customer by phone.
If a link in a possible phishing email is clicked, the recipient should disconnect from Wi-Fi, which could prevent malware (malicious software) from being installed on the computer; run an antivirus scan; and change passwords.
To combat phishing scams, Ruddock recommends turning to the experts.
“Hire a company that specializes in phishing training and make sure you’re taking the necessary steps to remediate and prevent future sophisticated phishing attacks,” he says.
Professor Jason Hong of Carnegie Mellon University’s Human-Computer Interaction Institute is one such expert.
“Security training is a lot like literacy…. It's something that you just have to do with every generation,”- Jason Hong, Professor at Carnegie Mellon University
In 2004, he and a team began researching phishing schemes and why people fall for them, backed by funding from the National Science Foundation.
“Back when we were doing this research, a lot of people didn’t think cybersecurity training could work at all because it tended to be really boring and dry,” he says. “We figured we could actually make it fun and interesting.”
Around 2007, Hong was part of a team at the university’s CyLab Usable Privacy and Security (CUPS) Laboratory that developed an online game called “Anti-Phishing Phil,” an interactive cybersecurity educational tool.
“It’s a game where you’re Phil the Fish and your job is to eat all the good worms and to avoid all the bad worms. And every worm has a web address associated with it and you have to differentiate between the good ones and the bad ones,” explains Hong.
As players navigate the fictional body of water dubbed Interweb Bay, they learn to recognize common phishing tactics.
“We’re trying to teach people how to read those URLs and to recognize a fake one,” he says.
There’s a tendency to believe that older, less tech-savvy people are more susceptible to phishing scams, but the university’s research doesn’t back up this assumption.
Hong recalls a Carnegie Mellon study of around 500 people, including students and faculty.
“Almost everybody thinks older people are more likely to fall for phishing scams, but our data shows actually the opposite, that, surprisingly, younger people are much more likely to fall for these scams,” he says.
Determining the reasons for the discrepancy would require a follow-up study for an official answer, he says, though he posits it could be because younger people “click on everything,” or because they just have less to lose than a more financially stable and, ostensibly, more cautious, older person.
Nearly two decades since his research began, Hong maintains phishing is the biggest cybersecurity threat to both businesses and individuals. Education on the topic must continue.
“Security training is a lot like literacy. We’re never going to solve literacy. It’s something you just have to do with every generation, and you still need lots of practice for people, too,” he says.
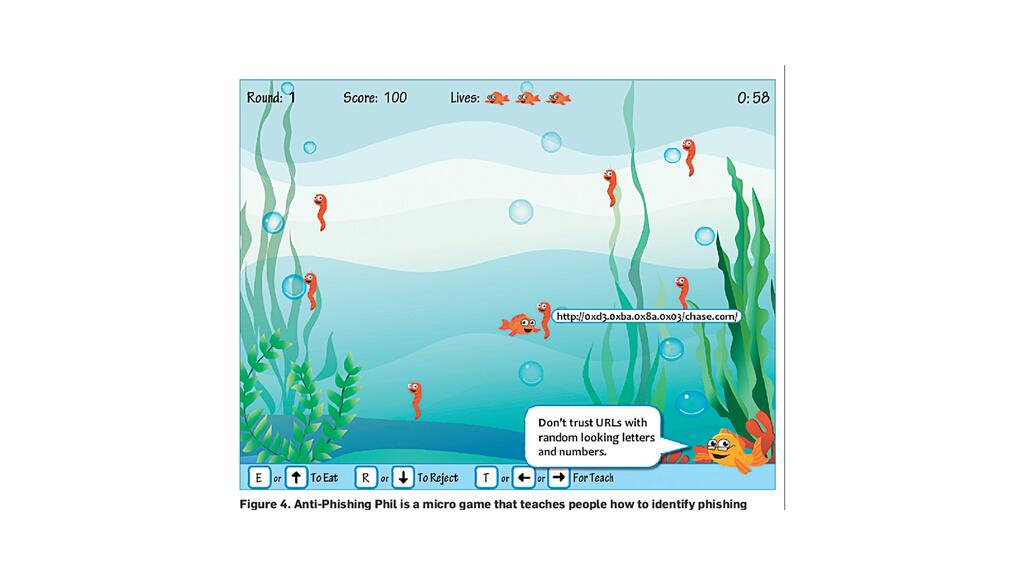
In addition to creating the Anti-Phishing Phil game, a screenshot of which is pictured above, Hong was a member of a team that developed a simulator that sent phishing emails to a company’s employees to see what could happen in real life.
Less than a quarter of small business owners send regular phishing test emails to employees, as per the Nationwide survey, but it’s something JSA’s Ruddock recommends.
“In the event an employee does click on a link, that’s really just an opportunity for enhanced training,” he says.
Not properly training oneself or employees about phishing scams could be a costly mistake.
Ruddock recalls a criminal case involving a man named Jimmy Sabatino, who is serving a 20-year sentence for his role in stealing more than $10 million in luxury goods from behind bars in 2014 and 2015.
As previously reported by National Jeweler, Sabatino, then an inmate in federal prison in Miami, pretended to be a music executive representing stars like Beyoncé and Justin Timberlake.
Using fake email accounts, he convinced major jewelry companies to send out pieces he claimed would be worn in music videos, sometimes via armored cars. His co-conspirators on the outside then picked up the jewelry and sold it at pawn shops.
The crew made off with a significant amount of jewelry, including a 7.29-carat oval-cut diamond and an 8.55-carat emerald-cut diamond.
“Companies should only be keeping the information that’s absolutely critical for them to conduct their business functions.” — Ryan Ruddock, Jewelers’ Security Alliance
In light of ransomware attacks, be mindful of data collection and storage.
Ransomware is a type of malware that encrypts files on a device, leaving users unable to access them until a ransom is paid.
In fall 2021, high-end jeweler Graff was hit with a ransomware attack and ended up paying $7.5 million to retrieve its data. The group of cybercriminals responsible for the attack, named Conti, released personally identifiable information about some of Graff’s customers before a deal was made.
The most common cybercrime reported to Jewelers Mutual is ransomware attacks, says Hansen, with policyholders requesting assistance to unlock their software.
Similarly, the company has had reports of a ransomware-like attack in which a jeweler’s social media accounts are hacked by criminals who request a ransom payment.
“Many jewelers’ businesses are supported by their social media platforms, particularly Instagram,” notes Hansen.
In contrast, JSA hasn’t received many reports of ransomware attacks, says Ruddock, but jewelers should still be aware of the possibility and protect their businesses.
“The No. 1 way you can protect yourself from ransomware is to make sure you’re backing up your data, particularly having offline, also known as cold storage, backups,” he says.
Many companies offer hourly or daily cloud storage backup services, he says, for as little as $10 per month.
Backing up data gives the jeweler control rather than depending on an outside entity—in the case of a ransomware attack, this means a criminal—to restore the service.
“Law enforcement has talked about [backing up] as being the best way to prevent ransomware, because if you’re backing up your data, you’re not going to have to rely on the attacker to decrypt your data.”
Another key tip for protecting a business from ransomware attacks is data minimization.
“Companies should only be keeping the information that’s absolutely critical for them to conduct their business functions. If you don’t absolutely need it to make a sale, you really shouldn’t have that information,” says Ruddock.
This especially applies to credit card information, he says, which customers should manually enter each time rather than using a “save card information” option.
“By practicing data minimization, you reduce the opportunity for a possible data breach, for an attacker to compromise your systems and then demand ransom.”
Keep an eye on tracking numbers.
A perhaps lesser-known cybercrime scam involves using the tracking number information issued by delivery companies such as UPS and FedEx to steal packages, so Ruddock advises keeping that information under wraps.
“The reason why you don’t want to share your tracking number is because the person who’s engaged in social engineering can take that number, and then they can actually reach out to your shipping company and have the package rerouted to any location that they want.”
If a customer calls for a tracking number, be sure to verify their identity before giving out that information to avoid having their package rerouted to an unintended recipient.
“By not giving out the tracking number, you reduce the opportunity for somebody to divert a package and to send it to a different location,” he says.
Jewelers also can talk with their shipper about how change of address requests are handled.
They can set a limit on the number of times an address can be changed on a shipment or request a package be returned to them if a change of address attempt is made.
Employees can work from home safely, if the right security measures are in place.
The COVID-19 pandemic led to more employees working from home and many have remained there, posing a new, but manageable, security risk.
“What we suggest is employees utilize VPNs, or virtual private networks, to make sure their communications are encrypted and away from prying eyes,” says Ruddock.
When employees use their personal devices to access company records, there are some security unknowns, like which websites they’re visiting, their downloads, potential malware, and a lack of antivirus protection.
“It’s increasing the opportunity for an attacker to potentially compromise your business systems if there’s no separation,” he says.
In addition to using a VPN, he recommends employees install antivirus and antimalware software on their computers and keep those programs up to date.
The same applies to employees who work from their personal cell phones. “If they are accessing company systems via their phone, it’s an increased challenge,” he says.
If an employer can afford to give employees work cell phones, says Ruddock, that’s the ideal scenario.
Regardless of where employees are working, Jewelers Mutual’s Hansen also recommends the use of access controls, meaning employers should determine the appropriate level of employee access to data, apps, and resources, giving necessary authorization only.
There should also be an incident response protocol in place so employees know who to reach out to in the event of a possible cybersecurity incident.
These are the tips and resources jewelers need to know.
There are many resources available for jewelers looking to learn more about cybercrime and how to prevent it.
It can be an arduous task, but Professor Hong proposes jewelers look into what’s known as their “threat model.”
“This is probably one of the most important concepts in computer security,” he says. “What are you trying to protect? Who are you trying to protect it from? And how important is it to you?”
What a jeweler spends on cybersecurity likely will be less than what they stand to lose by not protecting their business.
“Most cybersecurity is actually pretty basic, but putting it in practice is the hard part,” he says.
His recommendations include standard cybersecurity best practices, like setting up two-factor authentication on important accounts, particularly email accounts.
Hong advises creating strong passwords for key accounts, avoiding the reuse of passwords, and using a password manager to keep track.
Also, “Make sure you’re installing the software updates, the ones we all hate to do, but there’s a reason those software updates are there,” he says.
JSA’s Ruddock has a list of helpful websites for jewelers to visit (see below).
One of the most important resources, however, may be the insurance company. Prevention is key, but in the event of a cyberattack, cyber liability insurance could be a saving grace.
Jewelers should look into cyber liability insurance.
Jewelers Mutual, as well as many other insurance providers, offer products that will cover the financial and reputational fallout related to the impact of certain cybercrimes.
“A cyber event can result in a significant financial loss for a jeweler,” says Hansen. “Cyber liability coverage that steps in to indemnify a jeweler for their financial loss and pays for professional assistance to mitigate the damage caused by a data breach makes this coverage extremely important.”
Data breach and cyber-related protections can be added on to a jeweler’s block policy, providing coverage for privacy and security breaches, cyber extortion, cyberterrorism, or cybercrime, like phishing schemes. In some cases, insurance may even cover a ransomware payment.
“Our cyber liability coverage endorsement is already in place for many of our jewelers,” he says. “We expect jewelers are having more conversations about cyber coverage with their agents or brokers.”
This type of insurance can cover first-party losses, like money lost due to financial fraud, as well as liability claims, lawsuits, and regulatory penalties.
Many states require a business to notify customers if personally identifiable information has been released in a data breach, and that process can be costly.
Cyber insurance can cover the costs of that notification as well as fees related to recovering stolen data and restoring data and computer systems to their state before the cyberattack.
Some policies may also cover the cost of hiring a forensic information technology team to assess the extent of the breach and/or hiring a public relations firm to help a business’ reputation if news of a breach goes public.
“Customer and vendor relationships within the jewelry industry are built and sustained on trust. A cyber event can adversely impact this level of trust. Jewelers must invest in the training, software and insurance that best protects and assists with the risk of cybercrime,” says Hansen.
Cybersecurity Resources to Know
Implementing cybersecurity protections can be a complex task, but there are a wealth of tools available to small business owners. From software patches to security scans, here are a few helpful resources, as recommended by JSA’s Ryan Ruddock.
The Federal Communications Commission’s Cyberplanner helps small businesses create their own customized cybersecurity plans.
The Department of Homeland Security introduced a “Stop. Think. Connect.” campaign with employee training resources.
SoftwarePatch offers updated patches for computer and software applications. A patch is a change or update that can fix security vulnerabilities or other technical issues.
Fraud.org, created by the National Consumers League, also has helpful security tips and sends out fraud alerts.
The National Cybersecurity Alliance’s website offers free computer security scan tools for a PC or network.
IT security company Sophos has a news site, titled Naked Security, that sends out a daily newsletter with opinions, advice, and research on computer security issues and the latest internet threats.
The Federal Bureau of Investigation’s Internet Crime Complaint Center is a resource for reporting cybercrime. Jewelers can also reach out to JSA.
The Latest

Chicago police and members of the U.S. Marshals Service tracked down the 35-year-old suspect earlier this week in St. Louis.

Owners of the Ekapa Mine reportedly filed for liquidation about a week after a mudslide trapped five workers who have yet to be found.

A 10-year alliance has also begun to address the shortage of bench jewelers through scholarships, enhanced programs, and updated equipment.

Every jeweler faces the same challenge: helping customers protect what they love. Here’s the solution designed for today’s jewelry business.

The “Splendente” collection has evolved to feature hardstone letter pendants, including our Piece of the Week, the onyx “R.”


The jewelry collection belonged to “one of society's most glamorous and beautiful women of the mid-20th century,” said the auction house.

The update came as Anglo took its third write-down on the diamond miner and marketer, which lost more than $500 million in 2025.
With refreshed branding, a new website, updated courses, and a pathway for growth, DCA is dedicated to supporting retail staff development.

Emmanuel Raheb discusses the rise of “GEO” and the importance of having well-written, quality content on your website.

Each received around four years for burglarizing a jewelry store and a coffee shop in Simi Valley, California, last May.

Catherine Aulick, a GIA graduate, received the ninth and final Gianmaria Buccellati Foundation Award for Excellence in Jewelry Design.

We asked a jewelry historian, designer, bridal director, and wedding expert what’s trending in engagement rings. Here’s what they said.

Experts from India weigh in the politics, policies, and market dynamics for diamantaires to monitor in 2026 and beyond.

Beth Gerstein discusses the vibe of the new store, what customers want when fine jewelry shopping today, and the details of “Date Night.”

Are arm bands poised to make a comeback? Has red-carpet jewelry become boring? Find out on the second episode of the “My Next Question” podcast.

The Swiss watchmaker is battling declining sales amid a rapid retail expansion, according to a Financial Times report.

The campaign celebrates Giustina Pavanello Rahaminov, the co-founder’s wife and matriarch of the family-owned brand, for her 88th birthday.

Rachel Bennett, a senior jeweler who has been with Borsheims since 2004, earned the award.

After the Supreme Court struck down the IEEPA tariffs, President Trump imposed a 10 percent tax on almost all imports via a different law.

The industry veteran, who was with The Edge Retail Academy for 14 years, joins her husband at the company he founded in 2022.

The vintage signed jewelry retailer chose Miami due to growing client demand in the city and the greater Latin American region.

Former Flight Club executive Jin Lee will bring his experience from the sneaker world to the pre-owned watch marketplace.

Sakamoto, who died in mid-January following a sudden illness, is remembered for his humility and his masterful, architectural designs.

The April event will feature a new VIP shopping day requiring a special ticket.

Bulgari chose the British-Albanian singer-songwriter for her powerful and enduring voice in contemporary culture, the jeweler said.

In a 6-3 ruling, the court said the president exceeded his authority when imposing sweeping tariffs under IEEPA.

Smith encourages salespeople to ask customers questions that elicit the release of oxytocin, the brain’s “feel-good” chemical.